![COSO 2017]() This September, the Committee of Sponsoring Organizations of the Treadway Commission (COSO) published a much-anticipated update to their 2004 “Enterprise Risk Management—Integrated Framework,” a renowned and widely used risk management framework. The new release is formally called “Enterprise Risk Management—Integrating with Strategy and Performance.”
This September, the Committee of Sponsoring Organizations of the Treadway Commission (COSO) published a much-anticipated update to their 2004 “Enterprise Risk Management—Integrated Framework,” a renowned and widely used risk management framework. The new release is formally called “Enterprise Risk Management—Integrating with Strategy and Performance.”
The COSO update comes to meet the rising expectations of risk management, according to Bob Hirth, COSO Chair: “The complexity of risk has changed, new risks have emerged, and both boards and executives have enhanced their awareness and oversight of enterprise risk management while asking for improved risk reporting…Our overall goal is to continue to encourage a risk conscious culture.”
The risk landscape has changed drastically and will continue to do so. I often site the SEC’s Proxy Disclosure Enhancements as a proof point of this change. The Proxy holds boards explicitly responsible for their company’s risk management programs by requiring them to either adopt an effective ERM program, or disclose their risk management shortcomings. Other standards that underscore this transitional landscape is the Yates Memo, the IIA’s International Professional Practices Framework, and SEC Regulation S-K.
Failures in risk management have become all too common, and consumers, in addition to regulators, are taking action. Facebook and Equifax are poignant examples of this. Consumers will start to move their business and loyalty to institutions that can demonstrate effective risk management and governance because they are the only companies who will be able to prove their trustworthiness.
Managing risk has become undeniably complex and more imperative than ever before. However, frameworks like COSO 2017 provide a sense of assurance and a method to re-establish a world without catastrophic corporate scandals.
COSO 2017 Emphasizes Creating Value
The road to this restored confidence is enterprise risk management, which COSO defines:
“Enterprise risk management is not a function or department. It is the culture, capabilities, and practices that organizations integrate with strategy-setting and apply when they carry out that strategy, with the purpose of managing risk in creating, preserving, and realizing value.”
I couldn’t agree with this definition more. It touches on many attributes of ERM that I’ve long championed: integration across silos and levels, strategy and goal alignment, culture, and performance.
Another framework which I co-authored, the RIMS Risk Maturity Model (RMM), also emphasizes value. In fact, an independent study by Queen’s University, “The Valuation Implications of Enterprise Risk Management Maturity,” based on RMM data found that organizations with mature ERM programs realize a 25% market valuation premium over those in which “silo-based risk activities are dominant.”
Realizing this value, however, is more than a matter of understanding the theories presented by COSO 2017. It’s a matter of taking actionable steps towards aligning with those theories. It’s also a matter of prioritizing these steps, as it is often too big a task to take on all at once. Not all components presented by the COSO update contribute equal business value; those that contribute more value should of course be prioritized.
Below are some of the theoretical goals of the updated Framework that I resonate with most, as well as some helpful resources I’ve published that show you how to implement COSO 2017.
The enhancements are ordered by percent contribution to business value, as determined by “The Valuation Implications of Enterprise Risk Management Maturity” study.
Identifying Risks Across Departments
As put forth by the Framework, “Organizations that integrate enterprise risk management throughout the entity can realize many benefits including…increasing positive outcomes and advantage while reducing negative surprises: Enterprise risk management allows entities to improve their ability to identify risks and establish appropriate responses, reducing surprises and related costs or losses, while profiting from advantageous developments.”
While I wholly agree with this sentiment, I would also add that there is a crucial difference between risk outcome and root cause, as this distinction is vital to effective risk identification. All organizations must not only understand the distinction between risk outcome and root cause, but actively identify root cause instead of outcome. A fundamental problem in risk management is the identification of risk symptoms, not root-cause risks, which allows the initial problem to persist.
The Queens University study revealed that, statistically, an effective root-cause discipline and consistent uncovering of risks combine for 31% of ERM’s total valuation impact.
Related resource: 5 Steps for Better Risk Assessments
Using ERM to Enhance Performance
The COSO update emphasizes the correlation between risk management and enhanced business performance:
“Every entity has a mission, vision, and core values that define what it is trying to achieve and how it wants to conduct business. Some organizations are skeptical about truly embracing their corporate credos. But mission, vision, and core values have been demonstrated to matter—and they matter most when it comes to managing risk and remaining resilient during periods of change.”
COSO’s acknowledgment of performance as being intimately related to enterprise risk management is a key step forward for the industry. To go beyond a mere understanding of this principle, and to achieve its implementation, organizations must measure their board risk oversight by collecting internal metrics, uncovering trends, and using that data to execute strategy.
Performance Management, one of the seven attributes defined by the RIMS Risk Maturity Model, accounts for 23% of the market valuation premium.
Related resource: Meaningful Metrics: Using ERM to Inform Strategy
Integrating ERM Throughout the Organization
“Enterprise Risk Management—Integrating with Strategy and Performance” clarifies the “importance of enterprise risk management in strategic planning and embedding it throughout an organization—because risk influences and aligns strategy and performance across all departments and functions.”
The Framework itself is a set of principles organized into five interrelated components: Governance and Culture, Strategy and Objective-Setting, Performance, Review and Revision, Information Communication and Reporting.
I’ve always believed that organizations should not operate as a collection of independent silos. Instead, risk management should extend across all business areas and ultimately align with the corporation’s strategic objectives.
- First, there is the principle of cascading: risks, regulations, and objectives should trickle down to the most appropriate hierarchical level so that all managers can align their activities with high-level goals.
- Then there’s the principle of aggregation: Organizations must be able to aggregate front-line concerns and escalate them to the appropriate level.
- Finally, the principle of linkages: The reason ERM is so important, and so much more effective than siloed risk management, is that it identifies previously unknown links between departments.
This RMM attribute, ERM Process Management, is generally defined as “Integration into business processes to support the reduction of uncertainty and promote exploitation of opportunities.” It accounts for 20% of the total valuation impact brought by mature enterprise risk management.
Related resource: How to Integrate Governance Areas
Building a Healthy Risk Culture
The new COSO update clearly emphasizes the board’s risk oversight responsibility, a point many organizations need to improve upon. Boards need to foster the development of a risk-aware environment.
Too often, however, organizations emphasize aspects such as risk appetite too early and do not focus enough on areas that can be easily measured. Risk appetites, while useful, contribute less than 1% of the valuation premium, according to the RMM. Risk tolerance at the process activity level, however, is where the value is most gained because of its ability to be measurable and promote accountability.
The Queens University study determined that “the most important aspects of ERM from a valuation perspective relate to embedding discipline throughout the organization.” This attribute has an individual value contribution of 17%.
Related resource: 5 Steps Towards an Actionable Risk Appetite
What COSO Means for the Future of ERM
The new Framework also considers how businesses will have to adapt to keep up with the ever-increasing uncertainty in the business world. Regulations will always be updating, data will get bigger, and accountability will continue to increase.
Specifically, COSO 2017 references dealing with the proliferation of data, advising “advanced analytics and data visualization tools will evolve and be very helpful in understanding risk and its impact.” The Framework also mentions artificial intelligence and automations, stating “it is important for enterprise risk management practices to consider the impact of these and future technologies, and leverage their capabilities.”
I believe this future has already arrived. Instilling a sense of certainty and simplicity enterprise-wide is more than a one-person, one-team, or one-department job. Achieving a truly integrated approach to ERM and drastically enhancing performance already demands a powerful software solution.
Related resource: 7 Ways to Build the Business Case for ERM Software
The post How to Use the COSO 2017 Framework Update appeared first on insBlogs.
 The third step in the Risk Management and Own Risk and Solvency Assessment Model Act (RMORSA) is the implementation of a risk appetite and tolerance statement. This step is meant to set boundaries on how much risk your organization is prepared to accept in the pursuit of its strategic objectives.
The third step in the Risk Management and Own Risk and Solvency Assessment Model Act (RMORSA) is the implementation of a risk appetite and tolerance statement. This step is meant to set boundaries on how much risk your organization is prepared to accept in the pursuit of its strategic objectives. On September 7, big-three credit reporting company Equifax reported that hackers gained access to the personal information of about 143 million U.S. consumers, and have now recently reported that as many as 100,000 Canadian consumers were affected as well.
On September 7, big-three credit reporting company Equifax reported that hackers gained access to the personal information of about 143 million U.S. consumers, and have now recently reported that as many as 100,000 Canadian consumers were affected as well. Recently, Forrester Research published
Recently, Forrester Research published  The hot water in which Uber has been simmering has just reached new thermal heights. Back in
The hot water in which Uber has been simmering has just reached new thermal heights. Back in  This September, the Committee of Sponsoring Organizations of the Treadway Commission (COSO) published a much-anticipated update to their 2004 “Enterprise Risk Management—Integrated Framework,” a renowned and widely used risk management framework. The new release is formally called
This September, the Committee of Sponsoring Organizations of the Treadway Commission (COSO) published a much-anticipated update to their 2004 “Enterprise Risk Management—Integrated Framework,” a renowned and widely used risk management framework. The new release is formally called  2017 presented a whirlwind of corporate scandals:
2017 presented a whirlwind of corporate scandals: 

 Here we are. February 2018. For many, February is a trying month. How well are those New Year’s resolutions holding up? Have the early-morning January gym visits started to fade? Are salads getting old? Personal goals aside, here’s one thing we hope won’t decline: the excitement over your freshly finished 2018 budget.
Here we are. February 2018. For many, February is a trying month. How well are those New Year’s resolutions holding up? Have the early-morning January gym visits started to fade? Are salads getting old? Personal goals aside, here’s one thing we hope won’t decline: the excitement over your freshly finished 2018 budget. Oxfam, one of the UK’s biggest charities, was exposed this month to have had 87 claims of sexual exploitation and abuse involving its workers in the year ending April 2017, a 36% increase on the previous year.
Oxfam, one of the UK’s biggest charities, was exposed this month to have had 87 claims of sexual exploitation and abuse involving its workers in the year ending April 2017, a 36% increase on the previous year. The Forrester Wave
The Forrester Wave : Governance, Risk, and Compliance Platforms, Q1 2018 evaluates and ranks the 14 most significant GRC platforms available, and LogicManager has been named a Leader! But beyond measuring the current offering, strategy, and market presence of GRC providers, the report also dives into the current risk climate.
: Governance, Risk, and Compliance Platforms, Q1 2018 evaluates and ranks the 14 most significant GRC platforms available, and LogicManager has been named a Leader! But beyond measuring the current offering, strategy, and market presence of GRC providers, the report also dives into the current risk climate.
 On Sunday April 1, Retail group Hudson’s Bay disclosed that it was the victim of a security breach that compromised data on payment cards used at Saks Fifth Avenue and Lord & Taylor stores in North America.
On Sunday April 1, Retail group Hudson’s Bay disclosed that it was the victim of a security breach that compromised data on payment cards used at Saks Fifth Avenue and Lord & Taylor stores in North America. Wells Fargo has suffered the consequences of repeat scandals since 2016. This week, the bank agreed to a $1 billion settlement with federal regulators who have cited their lack of effective risk management practices as the root cause of their woes.
Wells Fargo has suffered the consequences of repeat scandals since 2016. This week, the bank agreed to a $1 billion settlement with federal regulators who have cited their lack of effective risk management practices as the root cause of their woes.

 This week, Wells Fargo launched a new ad campaign called Re-Established. The goal is to gain back customer trust after their repeat failures in risk management. It won’t work.
This week, Wells Fargo launched a new ad campaign called Re-Established. The goal is to gain back customer trust after their repeat failures in risk management. It won’t work. Chief risk officers and heads of operational risk responded to a survey held by
Chief risk officers and heads of operational risk responded to a survey held by 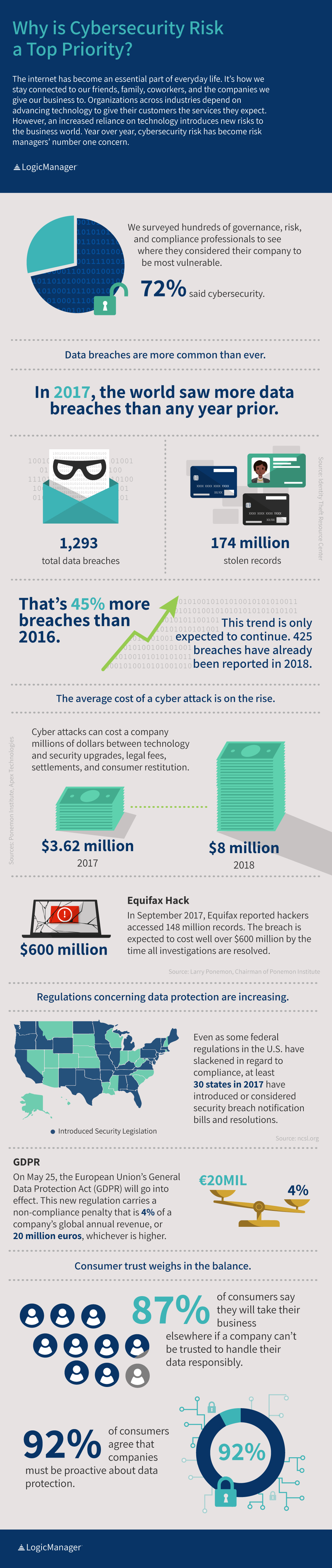
 Back in March, President Trump’s administration threatened to impose steep tariffs on imported goods from some of America’s biggest trading partners. In the following months, the administration set a 25% import tax on steel and 10% on aluminum.
Back in March, President Trump’s administration threatened to impose steep tariffs on imported goods from some of America’s biggest trading partners. In the following months, the administration set a 25% import tax on steel and 10% on aluminum.  Michigan State University has employed a new Chief Compliance Officer in response to the Larry Nassar scandal. By creating an Office of Enterprise Risk Management within the university, MSU is getting on the right track.
Michigan State University has employed a new Chief Compliance Officer in response to the Larry Nassar scandal. By creating an Office of Enterprise Risk Management within the university, MSU is getting on the right track. Risk management in the insurance business is a bit of a head scratcher. On the one hand, insurance companies are selling what many people consider to be a risk mitigation. On the other hand, insurance companies themselves face a variety of risks they need to mitigate.
Risk management in the insurance business is a bit of a head scratcher. On the one hand, insurance companies are selling what many people consider to be a risk mitigation. On the other hand, insurance companies themselves face a variety of risks they need to mitigate. The GDPR is the strictest set of data protection rules any nation has published, featuring some of the most severe penalties connected to data privacy seen yet. Now that the compliance deadline has passed, we started to wonder about GDPR readiness. How are companies stacking up to the new regulation?
The GDPR is the strictest set of data protection rules any nation has published, featuring some of the most severe penalties connected to data privacy seen yet. Now that the compliance deadline has passed, we started to wonder about GDPR readiness. How are companies stacking up to the new regulation?
 Since 2015, Chipotle has suffered multiple scandals of food-borne illness. The latest Chipotle outbreak has left more than 700 people ill. What does the Mexican grill have yet to learn?
Since 2015, Chipotle has suffered multiple scandals of food-borne illness. The latest Chipotle outbreak has left more than 700 people ill. What does the Mexican grill have yet to learn?